
[ad_1]
 Faced with a tsunami of pirated motion pictures and Tv reveals remaining accessed at will via thousands and thousands of piracy-enabled set-prime bins, enjoyment marketplace groups have experienced to appear up with a new anti-piracy approach.
Faced with a tsunami of pirated motion pictures and Tv reveals remaining accessed at will via thousands and thousands of piracy-enabled set-prime bins, enjoyment marketplace groups have experienced to appear up with a new anti-piracy approach.
The most important objective appears to demonize these equipment in the push, generating the effect that everyone utilizing them puts themselves in hazard, possibly thanks to fire risk or exposure to the perils of viruses and malware.
These statements are fantastic tabloid materials. Newspapers, specially in the British isles, gobble up push releases and rapidly spin them out, regardless of whether they have any substance to them or not. Though there is little proof that the scare stories are doing the job as a deterrent between the pirating masses, they are a steady resource of irritation for those people who know superior.
This week a new Kodi-related online video appeared on YouTube. Filmed at the RSA conference and offered by CyberScoop editor Greg Otto, it is made up of a brief job interview with Kurtis Minder, CEO of stability firm GroupSense. “How malware is developing on the Kodi/XMBC platform†was the matter.
Just after a brief introduction on so-referred to as ‘Kodi boxes’, Otto set it to Minder that his organization experienced been wanting into the “malware that has been floating by means of these boxes†and requested him to elaborate.
Minder claimed his enterprise commenced its investigation all around two months back, operating with the Digital Citizens Alliance (DCA). Of study course, DCA has been one of the principal resources of Kodi-similar malware tales, ostensibly for the defense of buyers.
Having said that, DCA is affiliated with the enjoyment industries and there is small question they are being utilised to boost an anti-piracy agenda. There is nothing at all inherently incorrect with businesses attempting to secure their articles, of study course, but executing so in a way that has the likely to mislead the public is bound to raise questions.
Back again to the video clip, Minder explained to interviewer Otto that his firm experienced been wanting at “what the attack footprint would be for malware on the media that would display up on any provided Kodi box that would be in someone’s dwelling.â€
It’s a curious assertion to speak about the streaming media alone offering an attack vector but Minder doubled down, stating that they’d found a number of destinations on the darkish world wide web “where people are offering malware-enabled media.â€
Otto didn’t check with Minder to elaborate on these claims and Minder did not respond to TF’s request for remark, so we still have no strategy what he’s referring to. However, Otto did pour fuel on the confusion by inquiring Minder about malware which involves abilities that no ‘Kodi box’ has.
“What happens with [that malware]? Is it a RAT [Remote Access Trojan] that takes more than a Television set that hooks up to a camera and is pretty much like spyware? Is it ransomware? What are we looking at?†he requested the protection professional.
“Some of that is [to be determined]we really do not know precisely what all of it does,†Minder responded. “But we do know there is a truthful amount that allow DDoS capability from the boxes.â€
We have no idea what constitutes a “fair amount†of malware but it sounds like many instances. Listed here on TF back again in 2017, we broke the news that a solitary Kodi addon was programmed to regularly go to the websites of rivals.
In that solitary case, the architect of that addon quickly apologized for his actions, the entire thing was concluded within a week, and we haven’t listened to of any related incident due to the fact. But Minder explained there are additional risks as well.
“There is malware that will really get more than some of the elements. We really don't know to what extent, if it’s really listening to the men and women in the home or not, that things has not actually been netted out,†he advised Otto.
Indeed, this sort of a detail has by no means been documented anyplace, not minimum given that “Kodi boxes†never have microphones. But immediately after additional prompting from Otto, Minder then went on to speak about Kodi set up on platforms other than Android units. His revelations about meant ‘Kodi malware’ in this respect are also controversial.
“The shipping and delivery mechanism [for the malware] seems to be two key approaches. It’s the Kodi platform itself, which signifies whichever you load that on. For occasion, if you did load that on an [Amazon] Firestick it could nevertheless be productive as an attack vector. The other a person is the streaming media alone. Embedded in the media alone there are some malware variants,†he reported.
As much as we know, malware embedded in streaming media that can be consumed via Kodi or in truth any standard media participant is unheard of these times. Nathan Betzen, President of the XBMC Foundation, the group at the rear of Kodi, instructed TorrentFreak that at least as much as he is conscious, this sort of a factor doesn’t exist.
“I’ve hardly ever listened to of malware in a video clip stream. I guess just about anything is possible, but to my understanding, there have been no experiences to that result,†Betzen reported.
Bogdan Botezatu, Senior E-risk Analyst at BitDefender, also advised TorrentFreak that he’d found nothing like that in the wild.
“Malformed video clip could leverage vulnerabilities in the player itself, but I’m not mindful of such assaults taking place in the wild,†Botezatu instructed us.
“Actually, the final time I noticed destructive videos dispersed via torrent web sites was years in the past, back in the days when Trojan.Wimad was earning the headlines.â€
Trojan.Wimad was a trojan uncovered in 2005 that was equipped to download distant data files from sites by exploiting the Electronic Rights Management (DRM) know-how obtainable in Home windows. The trojan bought on to users’ computers as a licensed-secured movie file. Kodi people are unquestionably not interested in individuals and in any circumstance, Android-centered Kodi bins are unaffected.
So, apart from the addon incident that lasted for a 7 days in 2017, we’ve never ever read of a live Kodi-associated malware assault anyplace in the wild. Betzen told us that he’d read of an occasion where by a coin miner had spread through 3rd-occasion code but that is an problem for hundreds of mainstream sites much too.
All that getting mentioned, we are not acknowledged as stability gurus, so we requested protection firm AVAST if they could supply facts on all Kodi-relevant malware incidents they have on document.
“Unfortunately, we have not noticed any Kodi-linked malware hazards in the wild,†AVAST Communications Manager Stefanie Smith explained to TorrentFreak.
Bogdan Botezatu at BitDefender also had no unique occasions to report.
“There has been a good deal of attention in the direction of Kodi in the past calendar year and most of the ‘security risks’ go all-around the truth that some addons let consumers to stream media straight from websites, so this is typically a legal situation somewhat than a cyber-stability a person,†Botezatu stated.
The BitDefender qualified did, nevertheless, issue us to a safety advisory from CheckPoint which specific a software package vulnerability affecting Kodi, VLC, and other players applying subtitles, which TF reported final calendar year.
“Kodi 17.1 was regarded to have been susceptible to a subtitle parsing bug that authorized an attacker to remotely control the Kodi box. This is a person of the most really serious threats I know of for the reason that third events could rig subtitles uploaded to different repositories and this would go unnoticed for a although,†he mentioned.
Whilst this vulnerability could have been employed for nefarious applications, there is no proof of it ever remaining exploited in the wild. And, in typical with all responsible platforms, Kodi and all other people involved fastened the difficulty before any destruction could be finished.
Going through our checklist of suppliers, TorrentFreak also questioned Symantec if they had at any time encountered any precise Kodi-similar malware. The organization explained to us they had almost nothing to report at this time but did spotlight the very same subtitle vulnerability pointed out by BitDefender.
To be clear, vulnerabilities can influence any software, including Home windows, but that doesn’t make them inherently dangerous to the purchaser as prolonged as they’re disclosed and then fixed in a responsible and timely manner.
However, listening to the enjoyment industries and those aligned with them, Kodi use presents an energetic and really serious malware danger to the general public, but a single with almost zero proof to guidance it.
Minder himself didn’t reply to our ask for for elaboration but we did control to acquire a duplicate of a presentation his enterprise ready for the Meeting of Western Lawyers Standard detailing meant Kodi threats. The document, dated Might 2018, tends to make for exciting reading through.
Most likely referencing the promises that Kodi malware is offered on the dark world-wide-web, the presentation slides exhibit an advert learned on the concealed ‘Dream Market’ market. The advert gives subscriptions to an illicit IPTV service but it is basically a person which is simply available on the typical open up web. Maybe most importantly, there is no mention of malware any where on the slide.
Dim world-wide-web IPTV but no malware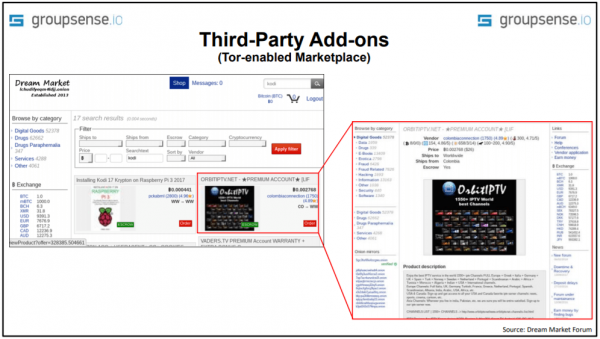
The upcoming slide proved intriguing considering the fact that it covers a subject matter very first released below on TorrentFreak at the get started of 2018. We discovered how some Kodi setups can be accessed by exterior functions if consumers aren’t watchful about the configurations for Kodi’s internet interface. Even though this is a regarded issue, this has practically nothing to do with malware.
Ultimately, the previous slide experienced this to say about Kodi and third-social gathering Kodi addons.
“Unbeknownst to the customer these thirdâ€party addâ€ons more introduces [users] to hazards this kind of as copyright violations, malware infection, disclosure of IP address and Net behavior, and the loss of the confidentiality of their communications,†the slide reads (PDF).
Even though it can not be argued that copyright violations can choose location, the ever-existing malware assert isn’t backed up by any publicly-accessible information indicating that these an event has happened a lot more than at the time or twice. To put that into viewpoint, the AV-Exam Institute suggests it registers in excess of 250,000 new malicious applications every working day.
In addition, IP addresses are usually disclosed no make any difference what content consumers access on the web, so that issue is moot too, together with the supposed challenges with confidentiality of communications. On the other hand, GroupSense has a lot more to add.
“Additionally, the interaction in between their Kodi application and the thirdâ€party addâ€ons are unencrypted and unauthenticated meaning that an attacker can introduce destructive code into the communication stream or compromise the thirdâ€party addâ€on just before the receiver (client) receives the knowledge thereby, infecting their system to include into a botnet or steal privileged details this kind of as consumer qualifications,†the slide reads.
We presented these statements to TVAddons, the world’s major repository of third-party addons and the developer of quite a few, previous and existing. They weren’t impressed with the claims.
“That argument is rather the stretch. Technically the identical would implement to any internet site you take a look at that does not use forced-HTTPS. Almost each individual unofficial increase-on repository is hosted by way of GitHub, which forces encryption,†the site explained.
“Kodi ‘boxes’ are made use of on property networks, not community Wi-Fi. By the time somebody could conduct a [Man-in-the-Middle] assault on your Kodi box, it would necessarily mean that they would have now had to compromise your router. If another person were to go by means of all that, they could very likely do a whole lot a lot more hurt devoid of even contemplating exploiting Kodi.
“Furthermore, most users use Kodi on their media containers, wherever very little to no privileged information would be present,†the web page added.
Let’s be crystal clear, just about every single piece of hardware and application, no matter if on or offline, can be exploited in some way by nefarious gamers or simply just the curious. Even so, the persistent assert that Kodi people are in some way under consistent malware assault is not borne out by any publicly available info.
In truth, just one of the world’s most popular anti-piracy vendors in AVAST suggests they have no document of ANY Kodi-similar malware. And Marius Buterchi, PR Manager at the very-respected BitDefender, couldn’t level us to any certain situations either.
“I just talked with the Lab fellas and they instructed me that they essentially haven’t observed any Kodi-linked malware in the wild,†he told us Friday.
With that, it now appears the excellent time to possibly place up or shut up in regard of “Kodi malware.â€
If there is malware out there impacting buyers of Kodi, security and amusement field providers building these claims need to back them up with good evidence due to the fact, as it stands, the horror stories seem to be built to frighten the masses, relatively than guard them.
The benefits of complete disclosure, detailing the Precise NAMES of the malware, WHEN they were being learned and by WHO, and what Particularly THEY DO, would be two-fold.
To start with, the purpose of scaring people away from Kodi would have far more effect, since the evidence of malware would be tough to ignore. That would be a major furthermore for the movie and Tv set industries who are fairly rightly involved about safeguarding their company.
Next, and just as importantly, Kodi users could just take actions to protect themselves, which should really be the quantity a single priority of any group, organization, or company that promises to be acting in the very best pursuits of buyers and the community in typical.
With that in head, we have an understanding of that the Digital Citizens Alliance will publish a new Kodi malware report in the coming weeks. Maybe it will contain precise proof of the malware staying spoken of continually in the media.
We would unquestionably welcome the publication of a certain and specific checklist of all malware variants in the wild which specially concentrate on Kodi end users. At that place, we can alert the important anti-virus and malware vendors who currently appear to be strangely in the dim.
The interview
[youtube www.youtube.com/watch?v=bRK13Xgt8c0&w=560&h=315%5D
[ad_2]



Be the first to comment